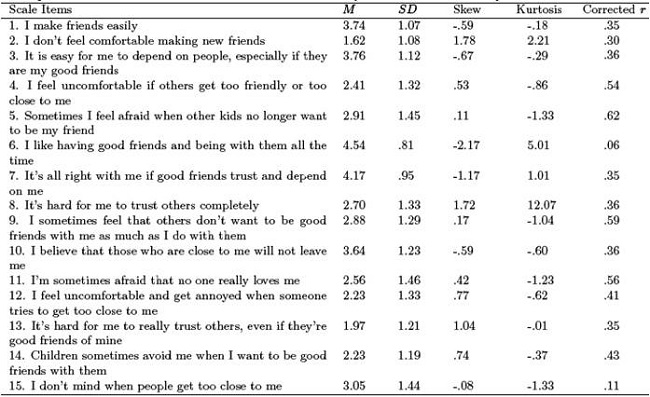
![PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cfec0b60ee965e255db5a86121bc2031c37642e5/10-Table3-1.png)
PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar

Man stopped at Reagan National Airport security checkpoint with 23 weapons | Transportation Security Administration
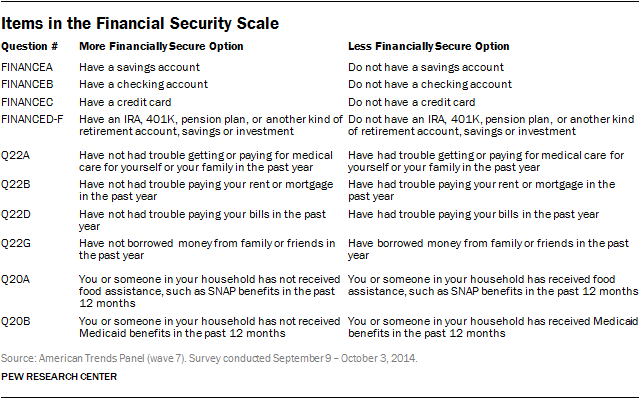
![PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cfec0b60ee965e255db5a86121bc2031c37642e5/7-Table1-1.png)
PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar

Robert M. Lee on Twitter: "In reply to my Sliding Scale of Cyber Security paper (https://t.co/8ojfeVyZ9r) @assante_michael "contributed" this: http://t.co/FS7dN9MAG2" / Twitter

Security at scale: Growing a security program regardless of headcount, size or budget | Security Magazine

Scales of Knowledge and Confidence in Safety, Security & Risk Assessments Must Include Calculations of What is Not Known, Unsure, Concealed or False

Frontiers | Measuring the Psychological Security of Urban Residents: Construction and Validation of a New Scale

Legal security concept with a justice scale of law protected by a blue umbrella as a security symbol of the judicial system in government and society in protecting rights and regulations Stock
![PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cfec0b60ee965e255db5a86121bc2031c37642e5/11-Table4-1.png)
PDF] Security, Reliance and Availability: Psychometric features of the Kerns' Security Scale in Hungarian population | Semantic Scholar